Rogue access points (article)
4.5 (108) · € 18.50 · In Magazzino
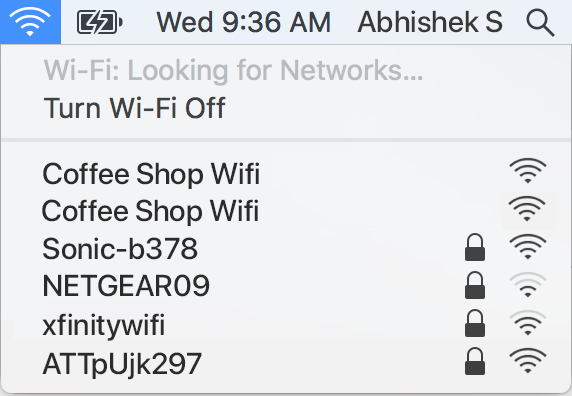
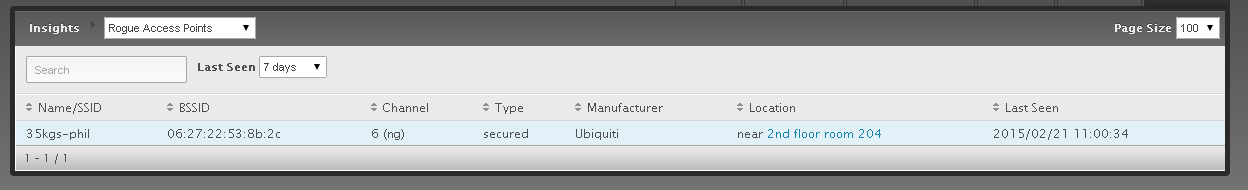
rogue access point Ubiquiti Community

PRAPD: A novel received signal strength–based approach for practical rogue access point detection - Wenjia Wu, Xiaolin Gu, Kai Dong, Xiaomin Shi, Ming Yang, 2018
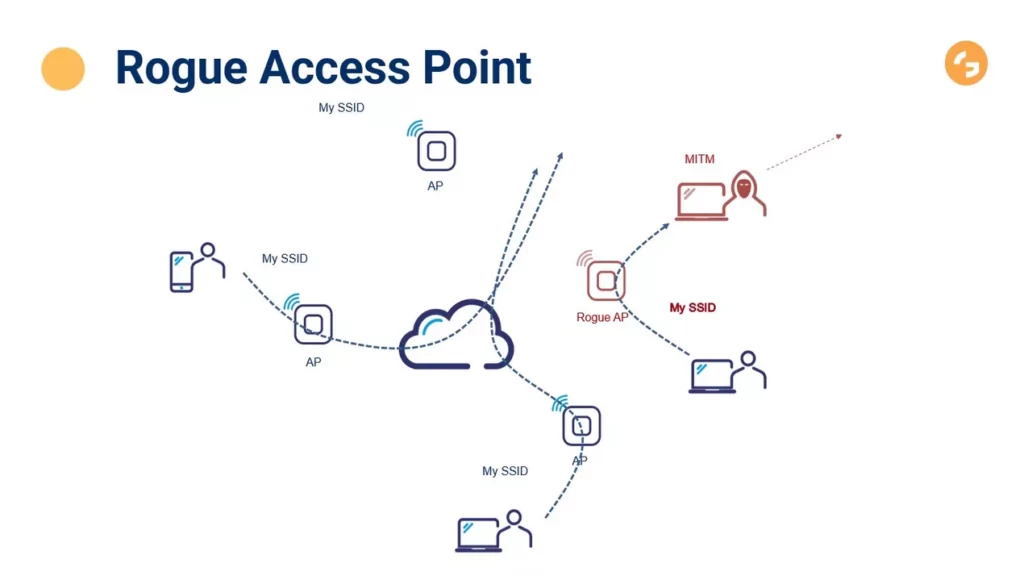
Security of wireless networks - how do hackers get in?

Rogue Access Points and Evil Twins - CompTIA Security+ SY0-501 - 1.2 - Professor Messer IT Certification Training Courses
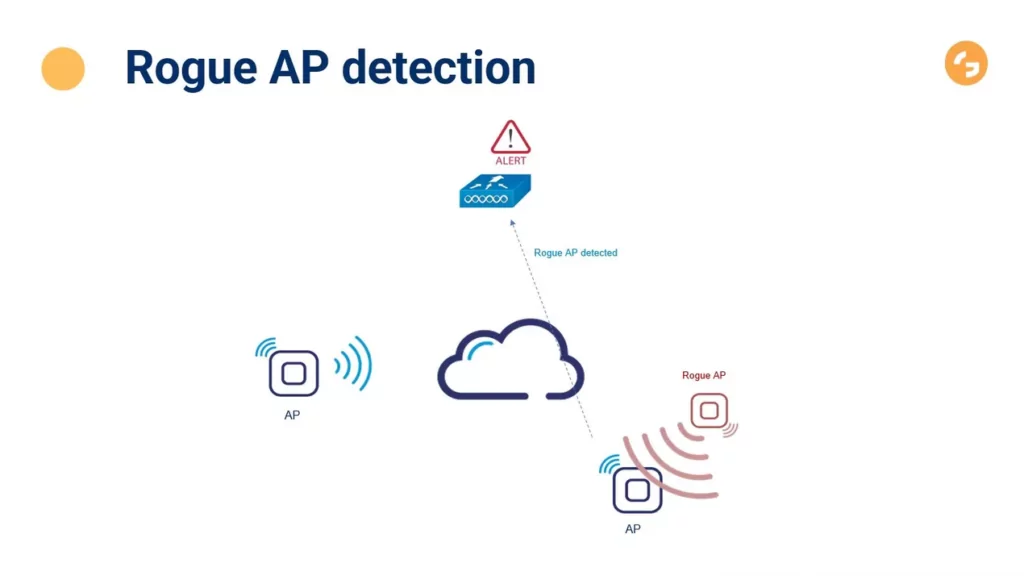
Security of wireless networks - how do hackers get in?

Instant On Rogue AP Management
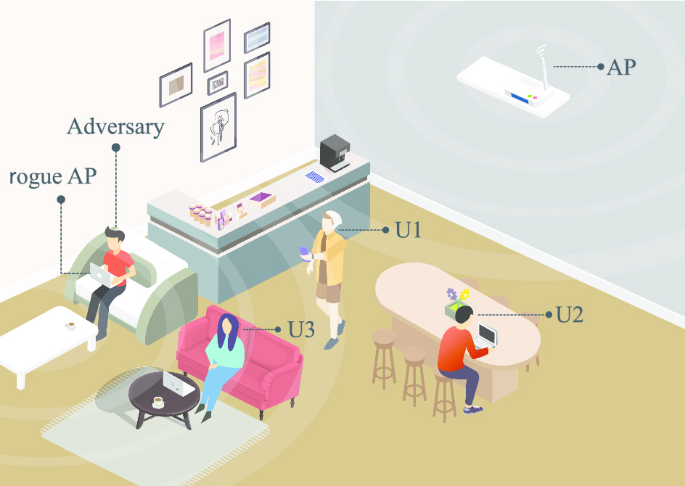
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis, EURASIP Journal on Wireless Communications and Networking
How to Protect Against Rogue Access Points on Wi-Fi
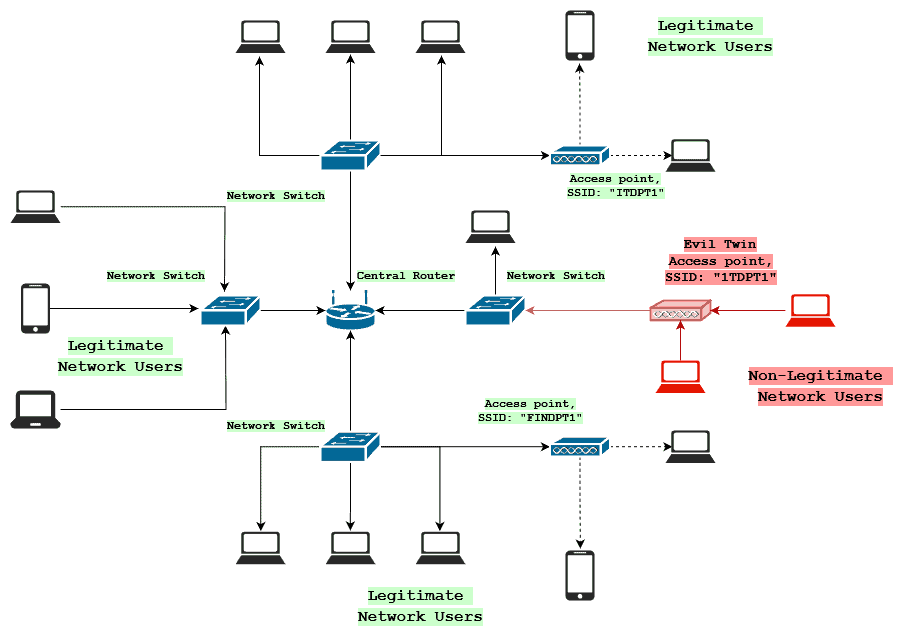
Networking: Rogue Access Points and Evil Twins
![Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17]](https://www.researchgate.net/publication/276230435/figure/fig3/AS:668979894951955@1536508644638/Unsecured-Rogue-Access-Point-Allows-Anyone-to-Connect-to-the-Network-17.jpg)
Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17]
Rogue Access Point Attacks

Rogue Access Points attacks - ppt download

The Danger of Rogue Wireless Devices and Access Points - Geek Speak - Resources - THWACK







