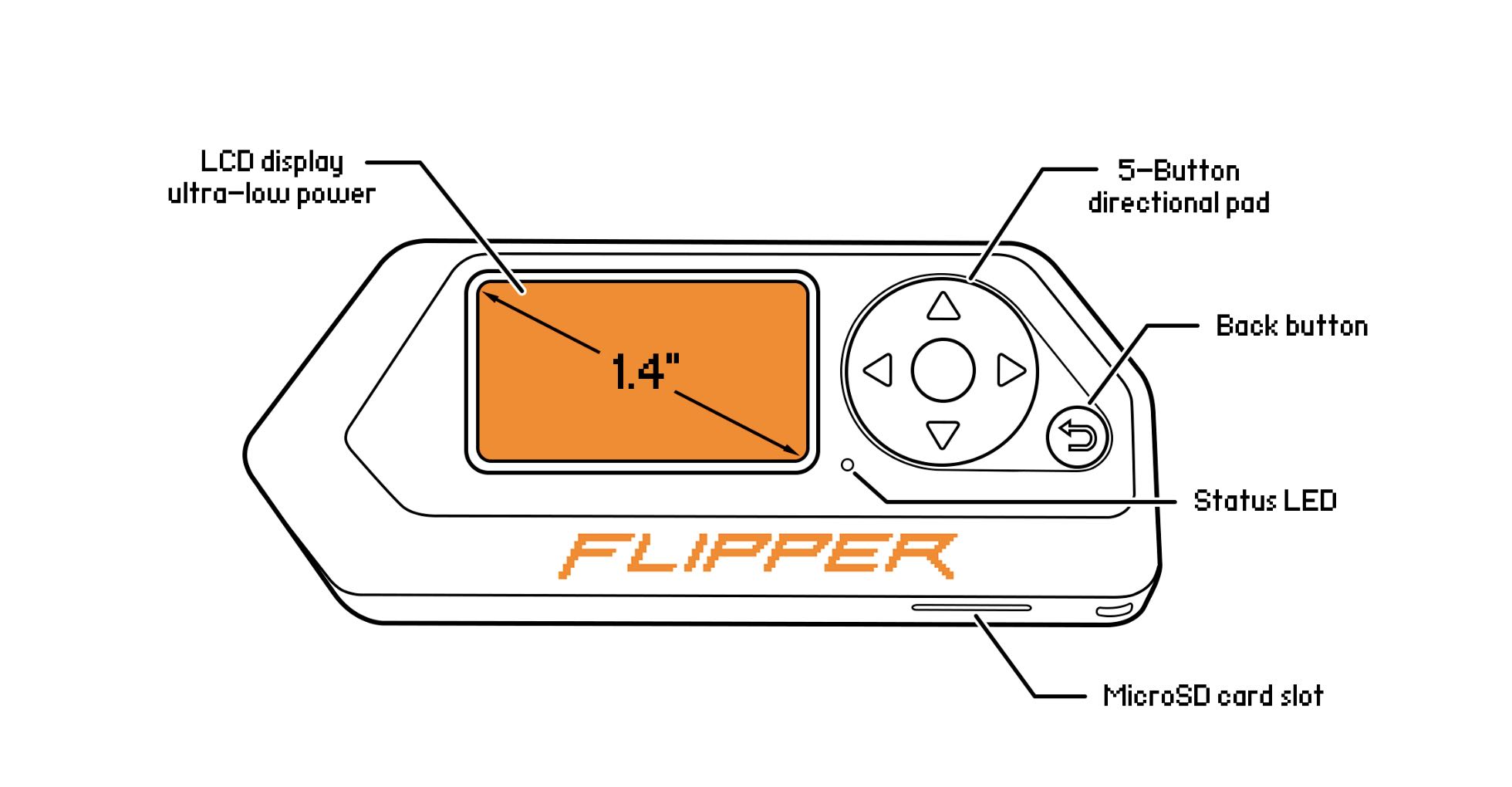
Exploring the Capabilities of Flipper Zero and Ubertooth One: Essential Tools for Wireless Security Testing (Part 1), by Jason Yee
4.6 (564) · € 16.50 · In Magazzino


Using SET to Simulate an Attack. We are going to have a look at the…, by Zuhayr Khalid

LINUX OPERATING SYSTEM. What is Linux?, by Muhammad Umer Kabir

Using SET to Simulate an Attack. We are going to have a look at the…, by Zuhayr Khalid

IP camera - Amcrest - Medium
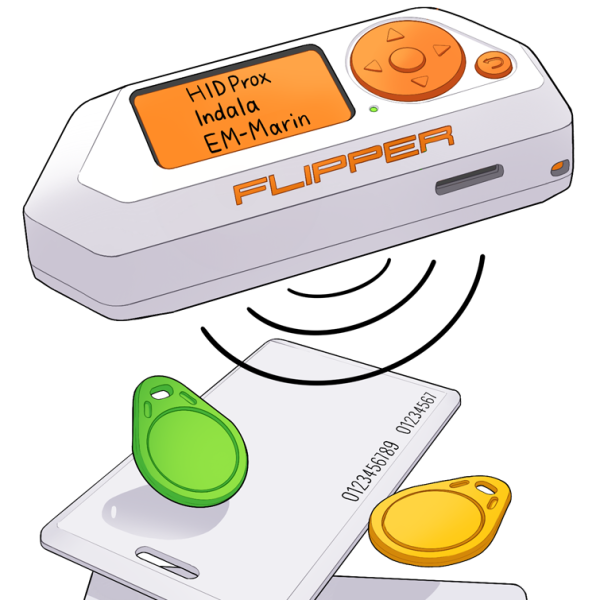
What's On Your Bank Card? Hacker Tool Teaches All About NFC And RFID, android cheat engine no root reddit
Why Industries are Switching to Linux So Quickly, by Maas Mohamad Ali
Techniques used for Firmware reverse engineering, by GMQureshi
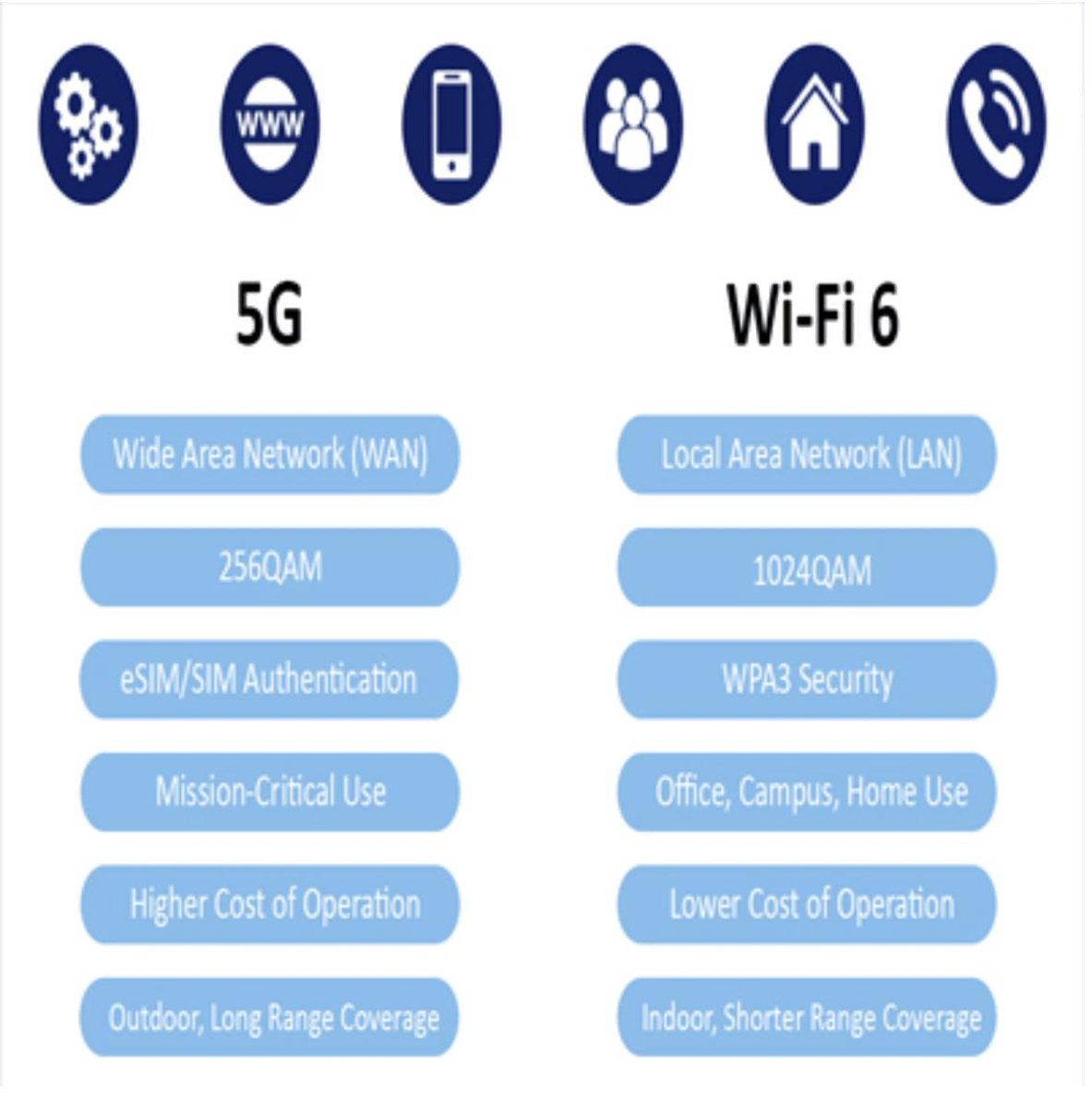
5G and WIFI 6:. A tech revolution?, by ACM GITAM

Using SET to Simulate an Attack. We are going to have a look at the…, by Zuhayr Khalid

Bluetooth Low Energy – InfoSec Write-ups

Exploring the Capabilities of Flipper Zero and Ubertooth One: Essential Tools for Wireless Security Testing (Part 1), by Jason Yee